MgtPro_8_QualityMgt
Quality Baseline/Goals
1. Functionality:
a. Suitability:
- The function of the sub-functions in the system should meet the principle of high cohesion and low coupling.
- The number of database table rows does not exceed 1 million rows, the maximum capacity of the database does not exceed 1000 GB, and the disk space needs at least 40G. 1000000.
- All the requirement should be implemented as requirement document says.
- The maximum number of transactions per day is 3,000.
- The average number of concurrent transactions is 20, and the maximum number of concurrent transactions is 50.
- The estimated number of users is 10,000, the number of login users per day is about 3000, and the bandwidth of the network is 100M bandwidth.
- The system can simultaneously satisfy 10,000 user requests and provide browsing capabilities for 25,000 concurrent users.
b. Accuracy:
- The data stored by the system should be atomic and persistent.
- The accuracy of the calculation is 7 digits after the decimal point.
c. Interoperability (Interoperability):
- The system should have good interaction with the delivery platform.
d. Compliance:
- Software coding should follow a uniform standard.
2. Reliability:
- There is a prompt for the input, the data is checked to prevent data anomalies.
- The system is robust and should be able to handle various abnormal situations that occur during system operation, such as human error, illegal data input, hardware device failure, etc. The system should be able to handle it correctly and avoid it properly.
- The probability that the service cannot be completed due to the failure of the software system is less than 5‰.
- The system is required to run 24 hours a day, and the continuous operation failure time of the whole year cannot exceed 10 hours.
- The system defect rate has a maximum of 1 failure every 1,000 hours.
- In 1,000,000 transactions, there is a maximum of 1 time when the system needs to be restarted.
3. Usability:
a. Learnability:
- Within 3 months of the introduction of the product, 60% of users should be able to use it to complete the transfer task within 45 seconds, the failure rate is controlled within one ten thousandth.
- 60% of users will realize that this is the bank’s online banking within 5 seconds of seeing the product for the first time.
- 80% of users can successfully buy a book within 5 minutes after receiving a half-hour system introduction training.
b. Operability:
- Some rural areas have poor network quality and low bandwidth. Guarantee the availability of the system under conditions of poor network environment.
- In 95% of the failures, the system takes up to 20 seconds to restart.
- Provide data backup and recovery functions to enable timely recovery and restore of data (provided by hardware and third-party software) when system data is lost due to system errors or other reasons or system data is corrupted.
4. Efficiency:
a. Time Behaviour:
- In 95% of cases, the general time response time does not exceed 1.5 seconds, and the peak time does not exceed 4 seconds.
- The time required for the positioning system to display from the click to the first interface must not exceed 300 milliseconds.
- When the network is unblocked, the time required to dial-up to the GPRS network must not exceed 5 seconds.
- When the network is unblocked, the website page refresh time does not exceed 10 seconds.
- In the recommended configuration environment: the login response time is within 2 seconds, the refresh response time of the column is within 2 seconds, the response time of the entry page list is refreshed within 2 seconds, and the response time of the information entry is turned on within 1 second, and the department and personnel list response is refreshed. Time is 2 seconds.
- Search during the off-peak hours according to the number and name specific conditions, and the search results can be obtained within 3 seconds.
b. Resource Behaviour:
- CPU usage <=50%.
- Memory usage <=50%.
5. Maintainability:
a. Changeability:
- After receiving the modification request, the general modification should be completed within 1-2 days; for the major demand or design modification after the assessment, it should be completed within 1 week.
- 90% of the BUG modification time does not exceed 1 working day, and the other does not exceed 2 working days.
- The circle complexity of the code must be within 10.
- Any method of any object does not allow more than 200 lines of code.
- Install the new version and keep all database contents and all personal settings unchanged.
- The product must provide tools to track any database fields.
b. Testability:
- The maximum circle complexity of a module cannot exceed 15.
- The delivered system must pass unit testing and be 100% covered.
- Development activities must use regression testing and allow for a complete test to be re-run within 12 hours.
6. Portability:
- The code change rate should be less than 20% when the system is migrated.
- The installation success rate should be greater than 90% when the system is transplanted.
- Functional integrity should reach 90% and above in the new target environment after system migration.
7. Security
- Strict access control. After the user is authenticated, the user can only access the data within the scope of his or her rights, and can only perform operations within its scope of authority.
- Different users have different identities and rights. They need to provide trusted authorization management services under the premise of authenticity of users, protect data from illegal/over-authorized access and tampering, and ensure confidentiality and integrity of data. Sex.
- Provide running log management and security auditing functions to track the historical usage of the system.
- Can withstand general malicious attacks from the Internet. Such as viruses (including Trojans) attacks, password guessing attacks, hacking, etc.
- At least 99% of attacks need to be detected within 10 seconds.
- Network delivery data should be encrypted. It is necessary to ensure that data is not sneaked, stolen or tampered with during collection, transmission and processing. Business data needs to be encrypted at the time of storage to ensure that it is not hackable.
8. Compatibility
- The system should support IOS, Android, Windows operating system;
- The system should support Oracle, DB2 database system;
- Up to 5% of system implementations need to be specific to a particular operating system.
- The average time to replace the relational database system is no more than 2 hours, and no data loss is guaranteed.
Quality Metric
The following metrics are majorly used for generating the daily/weekly status report with accurate data during test case development/execution phase and this is also useful for tracking the project status and Quality of the software.
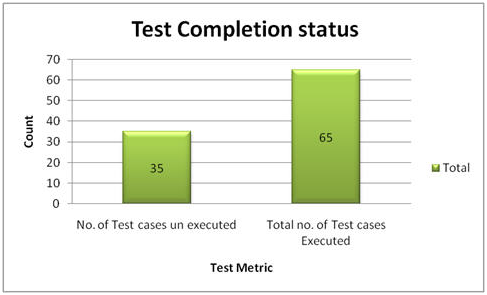
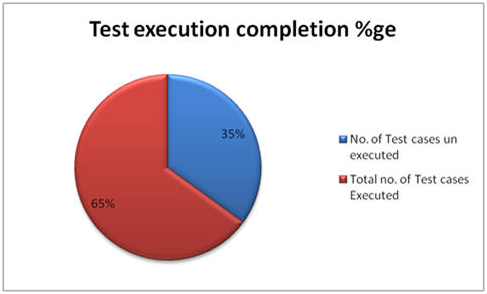
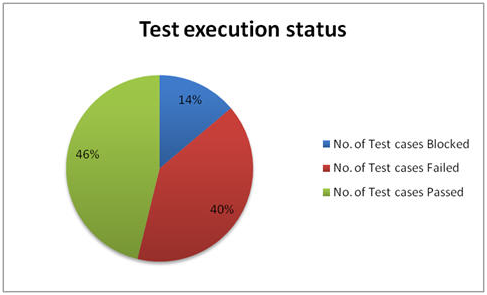
1. percentage Test cases Executed:
This metric is used to obtain the execution status of the test cases in terms of percentage.
2. percentage Test cases not executed:
This metric is used to obtain the pending execution status of the test cases in terms of percentage.
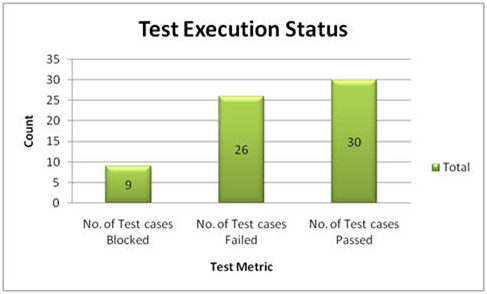
3. percentage Test cases Passed:
This metric is used to obtain the Pass percentage of the executed test cases.
4. percentage Test cases Failed:
This metric is used to obtain the Fail percentage of the executed test cases.
5. percentage Test cases Blocked:
This metric is used to obtain the blocked percentage of the executed test cases. A detailed report can be submitted by specifying the actual reason of blocking the test cases.


6. Defect Density
(Here “Size” is considered as requirement. Hence here the Defect Density is calculated as number of defects identified per requirement. Similarly, Defect Density can be calculated as number of Defects identified per 100 lines of code [OR] No. of defects identified per module etc.)
7. Defect Removal Efficiency (DRE)
DRE is used to identify the test effectiveness of the system.
8. Defect Leakage:
Defect Leakage is the Metric which is used to identify the efficiency of the QA testing i.e., how many defects are missed / slipped during the QA testing.
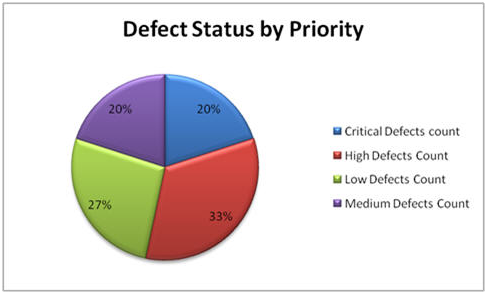
9. Defects by Priority:
This metric is used to identify the no. of defects identified based on the Severity / Priority of the defect which is used to decide the quality of the software.